Abstract: In order to solve the problem of large control overhead and low control efficiency of coarse-grained cryptographic logic array, based on the research of three-layer control model under the mainstream array processing architecture, a four-layer control model of array is proposed and correspondingly designed. Programmable control network. Control flow mapping for symmetric algorithms such as AES and A5-1 is implemented on a programmable control network of size 4 & TImes;4. In the 65 nm CMOS process, the DC synthesis results show a total area of ​​13 712 μm2, equivalent to an equivalent NAND gate of 0.95 million, accounting for 0.37% of the array area. The highest frequency of the mapped AES and A5-1 control streams is 1 389 MHz and 1 190 MHz, respectively, which meets the needs of small, fast applications. The four-layer control model and the three-layer control model are compared in six different performances. The former has far better performance than the latter, and can meet the high-efficiency control requirements of any network interconnection structure array.
introduction
The growth of network bandwidth and the diversification of network security protocols have led to the continuous expansion of password applications and the increasing performance requirements for cryptographic devices. For computationally intensive cryptographic algorithms, the data stream driven Coarse-Grained Cryptographic Logic Array (CGCLA) structure can make full use of its data parallelism and algorithm pipeline characteristics to achieve fast cryptographic operations and high flexibility. Performance requirements. However, in the face of such a flexible and efficient reconfigurable data path, if the array controller has low control efficiency, large delay and large area, the control time overhead is equivalent to the data path time overhead, so the control path may become a critical path, which will result in high cost. Problems such as poor scalability, so efficient controllers will be the key to CGCLA's performance.
In this paper, the control modes of three mainstream reconfigurable processing architectures are studied. It is found that the controllers of ADRES architecture have large scale and poor scalability. The control scope of XPP architecture has limitations, and the information exchange between control flows is difficult. The MorphoSys architecture has a single control flow and has the problem of large interaction overhead and storage overhead. Aiming at the control defects of the above architecture, starting from the structure of symmetric cryptographic algorithm, extracting the characteristics of control flow, using the full dynamic configuration information technology, a powerful four-layer control model is proposed and designed to CGCLA under the model. The programmable control network structure overcomes the problems of poor scalability, long interaction time, difficult information interaction, single control flow, and difficult mapping algorithm, which can well support the efficient control of block cipher algorithm and sequence cipher algorithm. .

At present, there are two main types of reconfigurable cryptographic processing architectures: array structure (ADRES [1], XPP [2], MorphoSys [3], S-RCCPA [4], etc.) and VLIW structure (Cryptonite [5], CCproc [ 6], RCB-CP [7], etc.). For the implementation of computationally intensive cryptographic algorithms, array structure data acceleration, resource utilization and other performance is better.
The ADRES architecture is controlled by a very long instruction word processor and belongs to a centralized control mode. It can perform periodic level switching of configuration information, but the long instruction word processor is too customized, resulting in large area size and poor scalability. The XPP architecture control mode is semi-centralized. Each array processing cluster can generate at least one control flow. By configuring page switching, it can achieve more flexible control than the ADRES architecture. However, when data flow graph or control flow graph interaction is required. When this architecture is not implemented or the implementation efficiency is low, it may cause problems such as difficulty in algorithm mapping and large interaction overhead between configuration managers. MorphoSys architecture can only generate a single control flow because only a single main processor controls the array. The parallel implementation of multiple cryptographic algorithms is very inefficient, which reduces the advantages of array data parallelism, and there is control and computation interaction time. Long, local storage overhead and other issues, so can not achieve efficient control.
The control models of the above three mainstream architectures are abstracted into three layers, as shown in Fig. 1(a), which is further improved and abstracted into a four-layer control model, as shown in Fig. 1(b). Between the configuration page layer and the reconfigurable array, a programmable controller is added, and the controller can receive feedback information of each processing unit, and select a configuration page according to the feedback information, thereby enhancing the information interaction capability between the data flow and the control flow, Improve control efficiency, but there are still problems such as poor scalability and single control flow, and this array-based configuration technology generates huge power consumption when configuring page switching.
The four-layer control flow model is further improved as shown in Figure 1(c). The control layer adopts a control network design based on the network interconnection structure, and each processing unit is assigned a programmable controller (PCE) capable of generating a simple control flow, and then combined with the three-dimensional configuration information technology [8] as an array. Each processing unit allocates storage space to store operator configuration information, and the improved four-layer control model can generate different or complex control flows through the programmable controller network interconnection, and can complete full dynamic configuration through three-dimensional configuration information technology. And can overcome the problem of large page switching power consumption caused by array configuration technology.
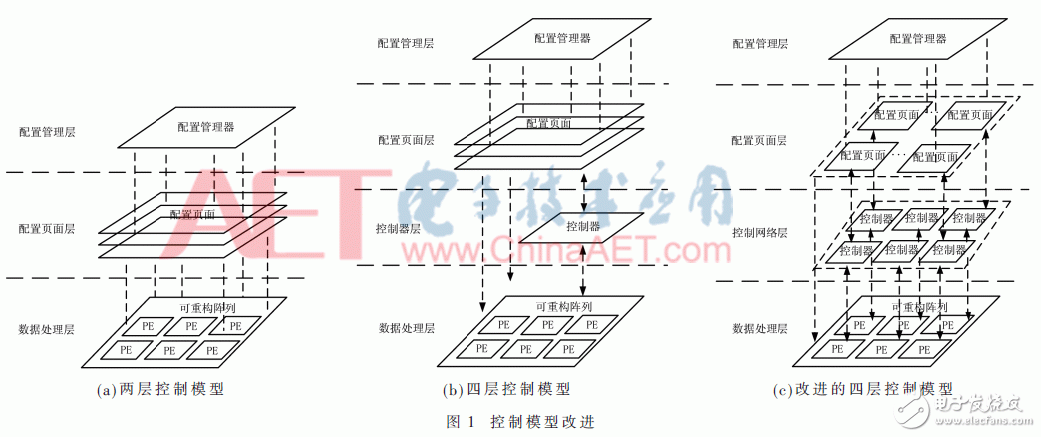
In order to design a suitable coarse-grained cryptographic array programmable controller, it is necessary to extract the appropriate control method based on the structural characteristics of the symmetric cryptographic algorithm.
2.1 Data stream multiplexing control
Whether it is the round operation of the block cipher algorithm, the memory component update of the sequence cipher algorithm, or the hash algorithm message expansion operation and the round operation, the iterative principle is satisfied, and the data stream exhibits a strong regularity: each operation is completely identical. The data stream, each group of intermediate data is only directly related to the next set of data.
2.2 unequal length data path control
Packet and hash cipher algorithms need to compute multiplexed data within a packet, as shown in Figure 2(a). Each channel of data may require different operations, and the operational data may be different. In order to ensure correct calculation results, there are generally two feasible solutions. The first one is to insert invalid operations into shorter paths and make them longer paths. The length is as shown in Figure 2(b). In the case of a large number of paths, this method becomes complicated and wastes resources. The second is to keep the original data unchanged by constantly assigning values ​​to itself, so as to stop the shorter data stream, as shown in Figure 2(c), wait until another data calculates the correct result and then switch to the next data flow graph. The operation is performed, that is, the original one stream map will be split into two sub-pictures. However, there are generally many ways of calculating the number of paths inside the hash algorithm, so the second method is not suitable. Here, based on the second way of using the sub-picture switching to implement the waiting, a register waiting mode is proposed. As shown in FIG. 2(d), synchronization of different paths is achieved by enabling the register. Compared with the first two methods, the resource utilization rate is improved, and the number of sub-pictures is also reduced, so that the control complexity can be reduced.
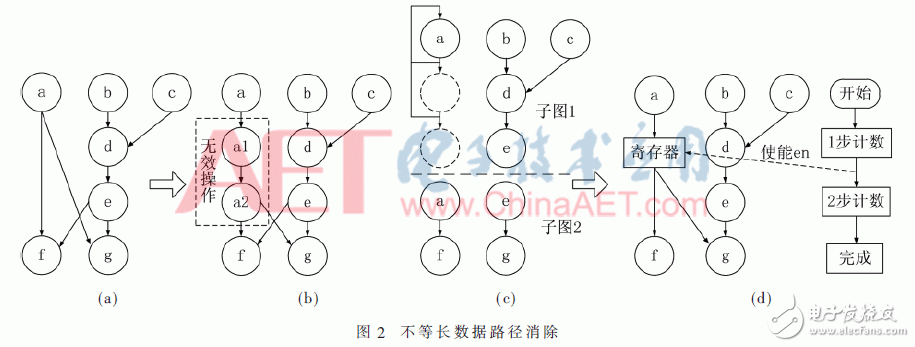
2.3 Switching Control
The symmetric cryptographic algorithm generally consists of multiple stages that perform different operations. The corresponding symmetric cryptographic algorithm global data flow graph generally consists of multiple different subgraphs. The block cipher algorithm can be divided into three stages: initial operation, round operation and output operation. The sequence cipher algorithm can be roughly divided into three stages: key input, memory component initialization and scrambling output, and each round of the hash algorithm is The exact same arithmetic structure, there is generally no phase division.
2.4 clock control, control structure control
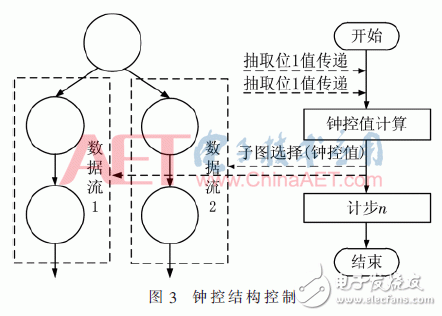
Unlike the block cipher algorithm, which has a certain data flow graph at any time, the sequence cipher algorithm has uncertainty due to the existence of the clock control model, which requires the data stream map to be temporarily determined in the operation, and a method is satisfied. The selection structure is adopted, and the two-way clock control operation is realized at the same time, which is equivalent to integrating the control flow into the data stream, so that it also has a fixed data stream, at the cost of requiring more resources, and the operation becomes more complicated. Another method is to pass the extracted bits required to calculate the clock control value to the control flow, and the control flow determines the data flow map selection according to the extracted bits, as shown in FIG. This method has fewer resources and simpler operations, but the relationship between control flow and control flow is more complicated.
MTU High Voltage Generators with MTU Diesel Engine, HV AC Generator
·Engine and alternator shall be mounted on a same frame steel skid.
·Small size, low weight, easy to operating, installation and maintenance.·World most famous brand diesel engine: MTU engine
·World famous brand High Voltage AC alternator: Stamford, Leroy Somer, Marathon, Faraday, etc
·Advanced and reliable controller: Auto start, AMF & Remote control by PC with RS232/485
·Full range protect function and alarm shutdown feature.
·Comply with ISO8528 national standard and ISO9001 quality standard.
. Voltage: 3kV, 3.3kV, 6kV, 6.3kV, 6.6kV, 10kV, 10.5kV, 11kV,13.8kV
Mtu Hv Genset,Mtu Hv Generator,,Mtu High Voltage Genset,Mtu High Voltage Generator
Guangdong Superwatt Power Equipment Co., Ltd , https://www.swtgenset.com
