The Montgomery power model operation is an algorithm for fast calculation of a^b%k and is one of the cores of the RSA encryption algorithm.
The advantage of Montgomery modular multiplication is that it reduces the number of modulo times (in the case of large numbers) and simplifies the complexity of the division (division in the hexadecimal power of 2 requires only a left shift operation). The modular exponentiation is the core algorithm of RSA, which most directly determines the performance of the RSA algorithm.
For the topic of fast modular exponentiation, Western modern mathematicians have proposed a large number of solutions, usually converting power-module operations into multi-module operations.
Here is a summary of the essence of the entire Montgomery algorithm. The Montgomery algorithm is not an independent algorithm, but a collection of three independent and interconnected algorithms, including
Montgomery multiplication model is used to calculate xâ‹…y (mod N)
Montgomery is reduced to calculate tâ‹…Ï−1 (mod N)
Montgomery power model is used to calculate xy (mod N)
The Montgomery power multiplication is the core part of the RSA encryption algorithm.
basic conceptCombing several concepts and imagine that a set is obtained after the integer modulo N
ZN={0,1,2,⋯,N−1}
Note: N has lN bits in base-b. For example, decimal and 100, both belong to base-10, because 100=102, so b=10. In decimal, the set of lN=3 of 667 is called the remaining class ring of N, and any x belonging to this set Z satisfies the following two conditions:
Positive integer
2. The maximum length is lN
The Montgomery algorithm mentioned in this article is used to calculate the operation based on the ZN set. Let me briefly explain the reason, because RSA is based on large numbers, usually 1024bit or 2018bit, and our computer cannot store the complete large number because It takes up too much space and is not necessary. Therefore, this encryption system based on large numbers of operations is based on the ZN set in the calculation. Naturally, the Montgomery algorithm is also based on ZN.
On the remaining class rings, there are two important operations, one is simple operation, which is addition and subtraction, and the other is complex operation, which is multiplication. We are more familiar with the operations on the natural number set. Let's look at how to evolve from the operation of a natural number set to the operation of a residual class ring.
For addition, if x±y (mod N) (0≤x, y<N) is calculated, imagine x±y on the natural number set.
0≤x+y≤2⋅(N−1)
−(N−1)≤x−y≤(N−1) We can simply convert N from the natural number to the remaining set by adding or subtracting N
The other type is the multiplication operation, that is, x⋅y (mod N) (0≤x, y<N), then
0≤x⋅y≤(N−1)2 If under the natural number set, let t=x⋅y, then we need to calculate for modN
The t−(N⋅⌊t/N⌋) addition and subtraction operation is very simple. The specific calculation here is not elaborated. We use ZN−ADD to represent the addition operation on the remaining class rings. Since we can do addition operations, then we can extend to multiplication operations, the algorithm is as follows
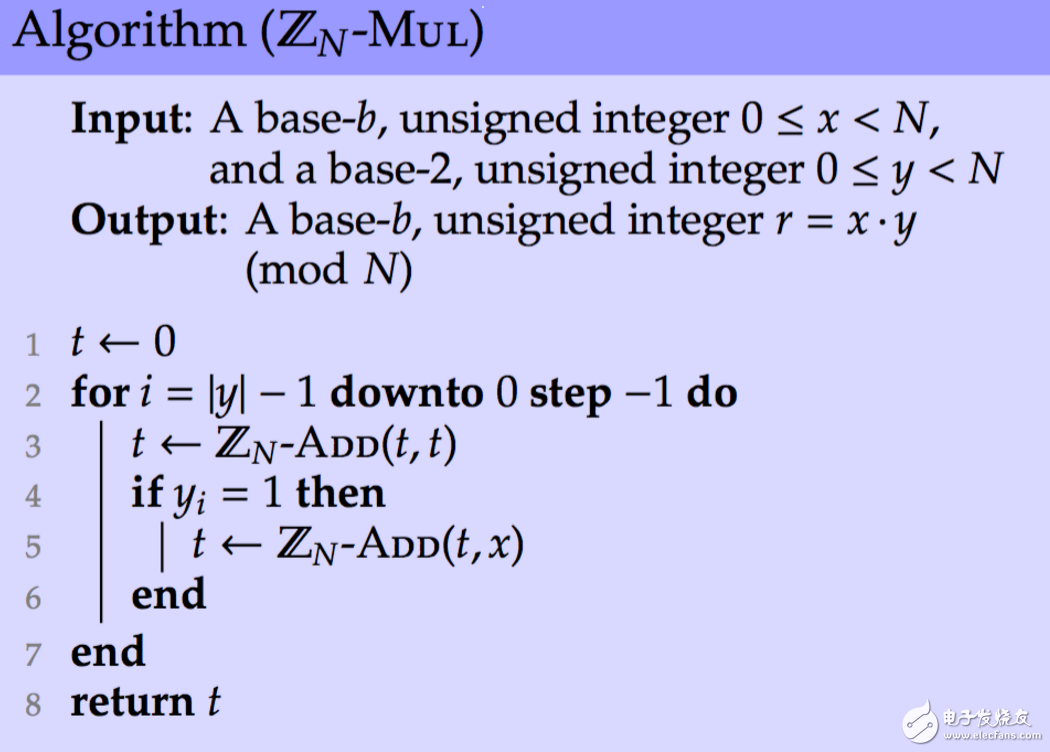
But this is not a good solution, because in general, we will not directly do the w-bit multi-bit operation, which will be replaced by Montgomery's multiplication instead.
For the modulo operation, there are generally the following methods1, according to the following formula, to calculate the modulo operation
T−(N⋅⌊t/N⌋)
This solution has the following characteristics
The entire calculation process is based on a standard digital representation
No pre-calculation is required (that is, some variables are calculated in advance for use)
It involves a division operation, which is very time consuming and complicated
2, using the Barrett reducTIon algorithm, this article does not elaborate, but has the following characteristics
Standard-based digital representation
No pre-calculation required
Need 2â‹…(lN+1)â‹…(lN+1) times multiplication
3, with Montgomery reduction, which is the algorithm to be discussed below, has the following characteristics
Not based on a standard digital representation (mentioned later in the text, based on the Montgomery notation)
Need pre-calculation
Requires 2â‹…(lN)â‹…(lN) number multiplication
The Privacy Screen Protector can display a black screen directly in front of the screen at an angle greater than 30° to effectively block the sight of people next to it, while achieving a perfect balance between black screen privacy and daytime clarity.
The Screen Protector can protect the edges and gaps of the display so that it can extend to the entire screen surface, thereby achieving maximum coverage without any exposed space.
The Self-Healing Screen Protector can provide the best protection for your phone from drops, bumps, scratches and normal wear and tear. Using an oleophobic waterproof coating can prevent sweat and grease from remaining on your fingerprints, keeping you simple all day long.
The 0.14mm thick Ultra-Thin Protective Film has a "real touch" feel and ensures fast response performance.
If you want to know more about Privacy Screen Protector products, please click the product details to view the parameters, models, pictures, prices and other information about Privacy Screen Protector.
Whether you are a group or an individual, we will try our best to provide you with accurate and comprehensive information about the Privacy Screen Protector!
Anti-peep Screen Protector, Privacy Screen Protector, Anti-spy Screen Protector, Privacy Protective Film, Privacy Hydrogel Film,Anti-peeping Screen Protector
Shenzhen Jianjiantong Technology Co., Ltd. , https://www.mct-sz.com
