This article describes the design of a regional home smart anti-theft alarm system. Intelligent anti-theft alarm system is mainly composed of four parts: wireless anti-theft alarm probe, home host, community host, regional host. Next one by one:
First, wireless anti-theft alarm probe design
The wireless anti-theft alarm probe is installed in various windows of the living room. It is small in size and low in power consumption. It can be directly attached to the window. When a thieves intruder is discovered, it can independently sound and light alarm and send a wireless alarm signal to the home console. The hardware structure is shown in Figure 1.
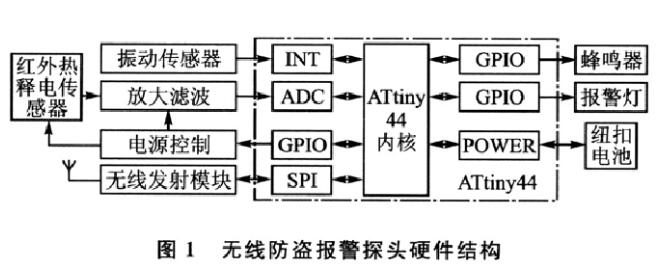
1, low-power design
The wireless burglar alarm probe is powered by a button battery and requires a low-power processor. This program selects Atreel's ATTIny44 processor. ATTIny is a low-power series product of Atmel Company, ATTiy44 has 3 kinds of low-power sleep modes that can be chosen separately, make ATTIny44 in the battery-powered device. There is a good performance. The application software can adjust the system clock frequency when needed to achieve optimal power performance, such as slowing down the clock frequency of some of the microprocessor's modules while the system is idle. With the AVR Power Stop System, users can disable timers, ADCs, and other energy-consuming modules when the user stops using the microprocessor. The ATtiny44 consumes less than 100 nA in Power Down mode. The size of the wireless sensor is required to be as small as possible in order to be installed, and the small package of the ATti-ny44 also makes the entire wireless sensor very compact. ATtiny44 usually works in the power-down state, and is the minimum power mode. When there is an alarm signal, the processor wakes from the interrupt to determine whether it is a thieves intrusion. If not, it returns to the power-down mode. If it is a thieves intrusion, the wireless transmitting module is started to transmit the wireless alarm information.
2, infrared pyroelectric sensor
In nature, any object above absolute temperature (-273 K) will produce an infrared spectrum. The infrared wavelengths released by objects at different temperatures are different. The infrared wavelength is related to the temperature, and the size of the radiation energy is related to the surface temperature of the object. . The human body has a constant body temperature, usually about 37C, and emits infrared light with a specific wavelength of about 10 mm. A passive infrared sensor works by detecting the infrared radiation emitted by the human body. The passive infrared sensor's sensor consists of two pyroelectric elements connected in series. The polarity of the two electrodes is exactly the opposite. The ambient background radiation has almost the same effect on the two pyroelectric elements, causing them to cancel each other out. The detector has no signal output. Infrared rays are concentrated by Fresnel filters and collected into pyroelectric elements. This element loses charge balance when it receives infrared radiation from the human body, and releases charge outwards. After detection processing, an alarm signal can be generated.
3, wireless transmission module
The wireless transmitter module of the wireless sensor is selected by Chipcon's CCII50 single-chip. ClI50 has a rich frequency resource and requires very few external components. The CCII50 has a sleep state. When there is no alarm information, it can be set to a sleep state to reduce the power consumption of the battery. When there is an alarm message, the wireless transmitter module is awakened and the wireless transmitter module is turned off after the alarm signal is transmitted.
Second, the home host design
The home host is the core of the whole family intelligent anti-theft alarm system. It can alarm itself after receiving the alarm signal, drive away the thieves, and send alarm messages to the community host and regional host to inform security personnel to arrive as soon as possible. The home host hardware structure is shown in Figure 2.
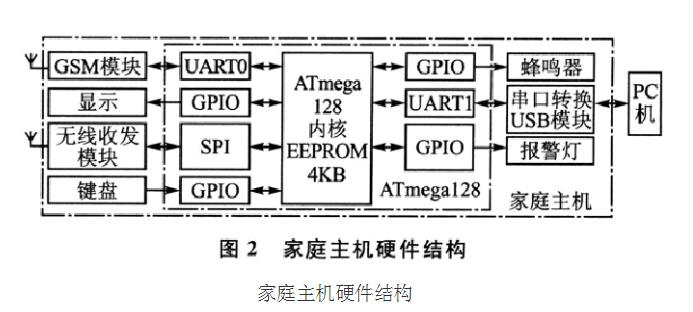
1, wireless transceiver module
The home host adopts Chipcon's CCIIOO wireless transceiver chip. The chip can be used with the CCII50 single-chip chip. It has abundant frequency resources and high receiving sensitivity, which can fully meet the indoor wireless sensor signal receiving task. When receiving the wireless alarm signal, CCII0O will transmit the received data to the single-chip microcomputer, the one-chip computer will analyze the data, and then send a sound and light alarm and SMS alarm information.
2, wireless sensor network
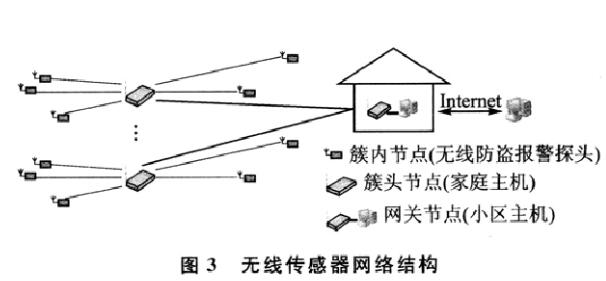
Wireless sensor network is a new information acquisition platform that can monitor and collect information of various monitoring objects in the network distribution area in real time, and send this information to the gateway node to achieve target detection and tracking within a specified range. It is characterized by rapidity and resistance to destruction. The regional family intelligent anti-theft alarm system utilizes the principle of wireless sensor network to set up a wireless intelligent anti-theft alarm network, in which the wireless anti-theft alarm probe is an intra-cluster node, the home host is a cluster head node, and the cell host is a gateway node. The alarm information of the wireless anti-theft alarm probe can be assembled to the community host in time, and the host of the community can respond in time so that the security personnel can respond quickly. Wireless sensor network structure shown in Figure 3.
3, microprocessor
The host computer has a slightly higher requirement for the microprocessor. The microprocessor simultaneously connects the wireless transceiver module and the GSM module and has a host computer communication interface. This scheme chooses ATmegal28 microprocessor, ATmegal28 has 2 serial ports, there is SPI interface, can meet the above-mentioned function requirement. In addition, it also has a rich 1/0 port resources that can be used to drive audible and visual alarms and relay actions. The ATmegal28 has a built-in 4 KB EEPROM that can erase 100,000 times. Because the home host needs to manage the location information and ID of the wireless anti-theft alarm probe, and store the alarm user's alarm phone, alarm message content, and alarm times, the 4 KB EEPROM can solve this problem well. After the microprocessor receives the alarm information from the wireless transceiver module, it needs to analyze the data, look up the list of activated wireless sensors, find the sensor corresponding to the ID number, read out the information, and insert the location information into the After the preset alarm message, it will be sent to the alarm user through the GSM module in turn according to the alarm user list.
4, GSM module
GSM network has high communication quality, good confidentiality, large network capacity and strong anti-jamming capability. It can achieve global automatic roaming and provide users with various services such as voice, data, and short message. It is currently the most mature and perfect in China. The widest coverage and most widely used mobile communication system. The short message of GSM network transmits information through the signaling channel and is unique to the GSM communication network. It does not need to establish a connection by dialing, and can directly send the information to be sent together with the destination to the SMSC of the short message service center, and the SMSC forwards the final destination to the short message service center at an appropriate time. The short message service, like voice transmission and fax, is the main telecommunication service provided by the GSM digital cellular mobile communications network. It transmits through the wireless control channel and completes the storage and forwarding functions through the short message service center. Each short message can send 70 Chinese characters, which can include the name of the alarm user, the specific address of the alarm site, and the location of the wireless burglar alarm probe. Clearly describe the location of the accident scene and ensure that security personnel can arrive at the scene of the accident the first time.
5, keyboard and display
The keyboard can be used to set various functions of the home alarm. Through the display, you can see the status of the home alarm host. Basic configuration operations can be set up through the keyboard, and some advanced settings need to be installed on the computer. Configure the software on the settings. The basic configuration can make the alarm system work normally, and some users who cannot use the computer can easily use this alarm system. Basic configuration operations include home burglar alarm switching, alarm user setup, activation activation and group management, wireless burglar alarm probe registration and activation activation, and simple alarm log management.
6, configuration software
The home console is equipped with configuration software that is installed on a home computer. The main functions of the configuration software are:
1 alarm user settings. You can set the alarm user's name, mobile number, and enable status. You can perform group management to distinguish the priority of different alarm users.
2 wireless burglar alarm probe settings. You can set the wireless alarm's ID number, the window position of the wireless burglar alarm probe, and the enabled status.
3 alarm message settings. Set the preset content of the alarm message. When there is a wireless burglar alarm probe sending alarm information, it only needs to insert the name of the owner and the position information of the wireless burglar alarm probe into the preset alarm message, and can directly send it to the GSM module.
4 alarm log management. You can view the details of the most recent alarm message and manage the alarm log information.
Third, the community host design
The main unit of the community is the user management in the residential community. The security coverage covers the entire community. It is suitable for installation by the community security department, and the entire community is monitored for security protection. The hardware structure of the residential host is shown in Figure 4.
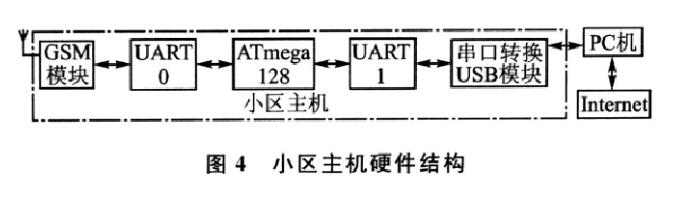
1, GSM module
Like the home alarm host, the cell host is equipped with the same GSM communication module. When the GSM module receives the alarm signal, it immediately sends the alarm information to the microprocessor, and the microprocessor transmits the short message information to the upper computer software through the serial port.
2, alarm function
The main function of the software is to display the alarm information transmitted by the microprocessor in a timely manner. At the same time, an audible and visual alarm is issued to remind the on-duty personnel to respond quickly and arrive at the accident site as soon as possible.
3, data management
There are many users in the community host and need to use a database for management. The upper computer uses sQL server for user data management. The upper computer software manages the users in the cell. When the user of the cell uses the alarm system for the first time, the user is required to send a registration short message to the cell host, or register the personal information with a manual input by the cell host, and establish a database of cell alarm users. . The upper computer software manages the alarm log and records each alarm in detail to facilitate subsequent searching.
Fourth, regional host design
The management of regional hosts involves the entire region, which may include several districts in the region. The users are larger and are suitable for installation by the local public security departments, which can effectively assist in the management of regional security. The hardware structure of the regional host is the same as the hardware structure of the cell host, but the host computer software function is more powerful and has stronger database management functions and a map positioning system. Due to the gradual expansion of regional host management, alarm methods may occur in parallel, so the most intuitive way to present is to be able to directly display the exact location on the map when an alarm occurs. Therefore, the regional host has good map data information. The geographic information data can be queried according to the address content of the alarm information, and the geographical location corresponding to the alarm information can be directly displayed on the map. If you can cooperate with the police force GPS positioning system, the police can quickly reach the scene of the incident, to minimize the loss of users.
Summary of Intelligent Security Alarm System Design Scheme (2)First, the overall composition of intelligent alarm system
The intelligent house anti-theft and fire prevention intelligent alarm system development and design proposal is based on the development of related technologies at home and abroad, and according to the actual conditions of China's housing construction, and the coordinated development of various related parties, in order to meet the living requirements of residents in the new era, truly intelligent The requirements of the alarm are determined.
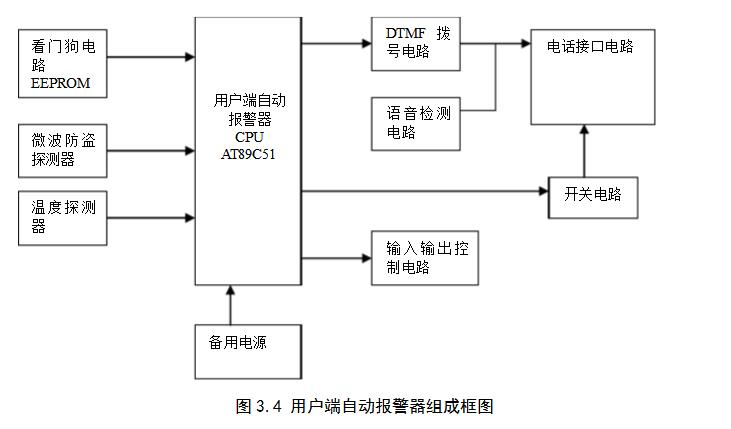
The anti-theft fire alarm system is a new type of electronic security alarm system. The design of the system is to combine electronic detection, intelligent control and telephone communication technology to form an anti-theft and fire alarm system. The overall system consists of three modules: anti-theft fire detectors, user-side automatic alarms and communication lines. The block diagram of the system is shown in Figure 2.1.
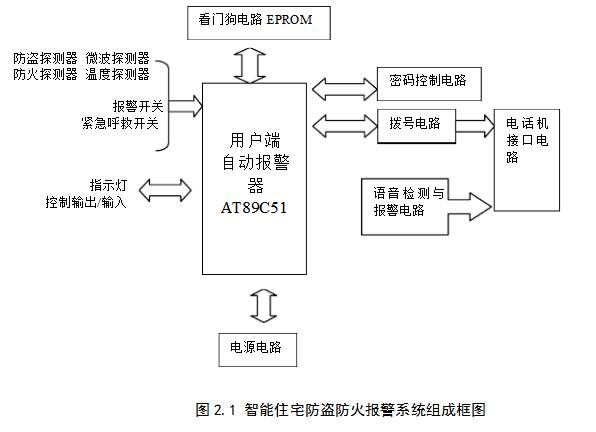
Customer-side automatic alarms are installed in residential buildings to monitor and control different types of detectors in different parts of residential buildings and to process data collected from various detectors. When an abnormal situation occurs, an alarm is automatically dialed through the telephone line in the home and a connection with the central controller is established. The system does not need to occupy the telephone line separately. When there is an alarm signal, the alarm phone enjoys the priority of the telephone line.
The basic working process of the system:
The user's protection site, once an intrusion, or a fire and other emergency situations, with the corresponding alarm detector (a variety of fire, anti-theft and manual alarm buttons, etc.) will immediately send an alarm signal to the user-side automatic alarm. After receiving the alarm situation, the automatic alarm device will immediately confirm (multiple inspection interrupt signal), if no alarm is released after 50s and the alarm condition is confirmed, the live alarm (buzzer) and light ( LED) alarm, while the user-side automatic alarm automatically dials the pre-set alarm phone number to the relevant department for voice alarm 2. On the panel of the user-side automatic alarm, there is an LCD display, a keyboard, and a three-color warning light (LED). The three-color warning lights indicate the status of the fire or burglar alarm of the fire or infrared/microwave double-check, normal operation and system failure status. , That is the warning light (red), work light (green) and fault light (yellow). The LCD shows the time when it is normal, and the time when the event occurred is locked. The user-side alarm device also has a probe failure alarm function to avoid missing reports due to power failure of the probe, and to turn on the fault lamp when a fault occurs. If the probe is judged to be dropped (sheared), an audible and visual alarm is issued. If a false trigger occurs and an alarm occurs, it can be released by triggering the delay time (505 timer). In addition, the user-side automatic alarm also has status information (such as whether there is AC power, whether the backup battery power is insufficient, etc.). The reporting function can be used to alarm the default ordinary telephones and mobile phones.
Second, hardware system design
The software of the automatic alarm software adopts a modular design and is divided into a main control module, an off-hook module, a dialing module, a voice module, a display module, and a read-write data module. Using assembly language programming, in the KeiluVISion2 environment, use the Top 2000-B programmer to write the program to the microcontroller. The software design of the programming language adopts MCS-51 assembly language to write the relevant program in the automatic alarm (such as dialing, pronunciation, reading and writing X25045, etc.).
1, anti-theft detector circuit design
The microwave detector is a space detector for detecting any moving objects in the defense space. Microwave detectors have high reliability, no light and heat sources, and low detection environment requirements. In the microwave section, when transmitting at a frequency, within the range covered by the microwave energy, if there is an object moving, it will be reflected at another frequency, so that there is a frequency difference between the transmission frequency and the reflection frequency. This frequency difference is related to many factors, including the speed of the moving object, and the radial angle of the detector.
In an actual circuit, an oscillator circuit generates and emits near-microwave electromagnetic waves to form a microwave field. The antenna converts the electric signal to a corresponding electromagnetic wave and radiates into the surrounding space. The radiation radius can reach more than 10m (if you want to continue to increase the radiation radius or increase Sensitivity can be achieved by adjusting the size and direction of the antenna.) When someone moves in the field, the reflected microwaves will change in frequency, so that the microwave detector outputs a low-frequency electrical signal related to the speed of the human body. According to this characteristic, microwave detectors are also selected for the detection of robbery.
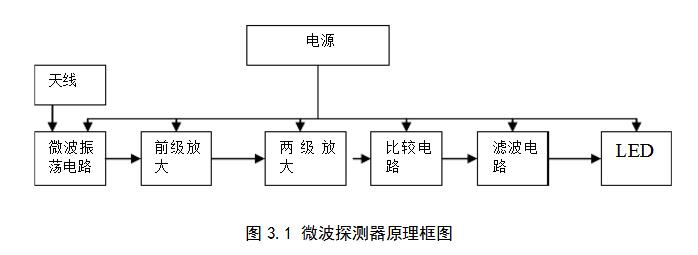
The loop antenna and its surrounding resistors, capacitors, and MOS FETs form a near-microwave high-frequency self-oscillating circuit (whose oscillation frequency is around 1 GHz). The principle of the microwave detector is shown in Figure 3.1 when the circuit is turned on. Later, the single-frequency, equal-amplitude signal generated by the oscillation is transmitted to the space through an external antenna to generate a three-dimensional space microwave protection zone. The antenna transmits both an oscillation signal and an echo. The reflected microwave signal is mixed with the original signal to generate a weak frequency shift signal, and the signal is sent to the amplifier for amplification.†The amplified signal is sent to the input window of the amplitude comparison input, and the detected signal with a certain intensity is converted after comparison. It is a constant-amplitude pulse output with a different width.
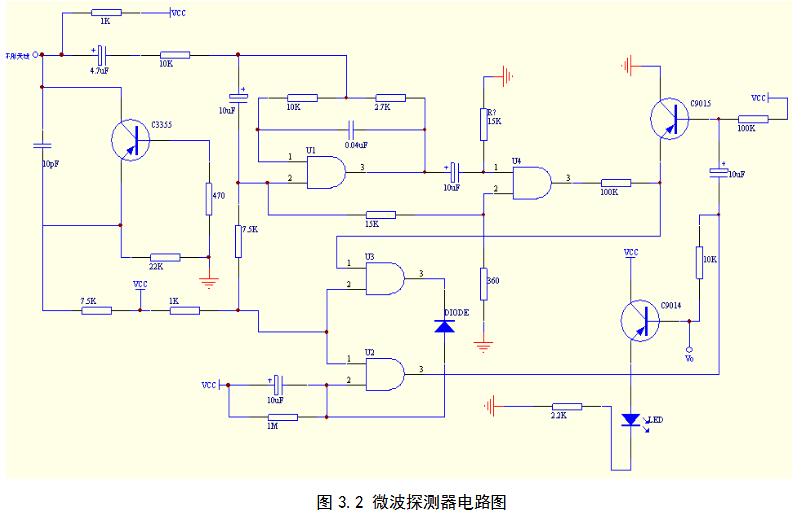
The main components used in the microwave detector circuit are the single-supply universal operational amplifier KIA324P, the loop antenna, the microwave oscillation tube C3355 and some peripheral components, and an external +6V power supply. Its circuit diagram is shown in Figure 3.2. When someone moves within the microwave protection zone, the frequency and amplitude of the oscillation change accordingly. According to the Doppler effect, the frequency of this fluctuation is related to the speed of the object movement, and the amplitude is related to the distance. After the mixing, the high-frequency signal loses its function because the signal is too high, and the weak low-frequency signal is amplified by U1. The charging circuit is formed by a 10 pF capacitor and 7.5 K resistor, and the charging voltage is used as the reference voltage of the first-stage comparator U4. At the same time, the delay function is realized, that is, when the preamplifier voltage is higher than the reference voltage, the output is high level. At this time, C9015 is turned on, and the final signal is detected by comparing the window comparator formed by U2 and U3. Signal [2. During the experiment, the alarm range is about 7-8 meters. When a valid signal is detected, there is a 20-second alarm signal output. The LED light indicates an early warning and can be effectively detected in real time. The circuit can operate over a wide range of voltages (standard voltage is 32V, but it can actually operate over a wide range of voltages). When an anomaly signal is detected, it is leveled.
2, fire detector circuit design
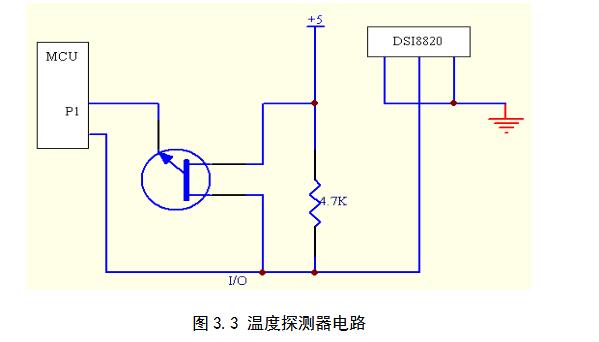
The temperature detector uses a digital temperature sensor DS18B20 with a 5V DC voltage supply. DS18BZ0 temperature measurement principle is the use of temperature-sensitive oscillator frequency with the temperature changes, the temperature signal is directly converted to a serial digital signal, through the internal counter temperature oscillator cycle count can achieve temperature measurement. The DS18B20 uses a parasitic power supply to ensure sufficient current is available during the active DS18B20 clock cycle. Figure 3.3 uses a MOSFET and I/O port of the MCU to complete the bus pull-up of the DS18B20, and then through another An I/O controls the DS18B20 and obtains the temperature value.
3, the overall design of the user-side automatic alarm
The user-side automatic alarm is the design focus of this topic, and the auto alarm is composed of a block diagram as shown in Figure 3.4. It mainly includes the dial-up module, voice module, telephone interface module, keyboard/password display module, and power supply module. The alarm function is already in place. Section 1.2 has been specifically described. It will not be described in detail here. This section focuses on the hardware circuit design related to the automatic dialing function.
The system microprocessor adopts AT89C51 single-chip computer that American ATMEL Company produces. The AT89C51 adopts the COMS technology and is a low-power, high-performance, 8-bit microcontroller fully compatible with the INTEL 8051 series microcontrollers.
The AT89C51 has 4K bytes of Flash (Flash) memory, which can be erased repeatedly. In the design process, the original program can be repeatedly modified, compiled, and programmed into the SCM, which is suitable for the development and development of the SCM minimum system.
1) Automatic alarm circuit design
The automatic alarm circuit is shown in Figure 3.5. The clock circuit consists of two 30P capacitors and a 12MHz crystal. The reset circuit is composed of a resistor, a capacitor, a diode, and a key switch, and has a function of power-on reset and manual reset. The INTO and INTl of the microcontroller are connected to the theft and fire sensors respectively to achieve the acquisition of various alarm conditions. In order to prevent the impact of the environmental interference signal on the triggering interruption, when the response is interrupted, the interruption signal is checked multiple times (for example, 5 times), and when the interruption signal is confirmed, the interruption processing subroutine is executed, otherwise it is considered that the outside interference signal is not Perform alarm processing to effectively reduce the chance of false alarms.
The system microprocessor adopts AT89C51 single-chip computer that American ATMEL Company produces. The AT89C51 adopts the COMS technology and is a low-power, high-performance, 8-bit microcontroller that is fully compatible with the INTEL 8051 series microcontrollers. The AT89C51 has 4K bytes of Flash (Flash) memory, which can be erased repeatedly. In the design process, the original program can be repeatedly modified, compiled, and programmed into the SCM. This is suitable for the development and development of the minimum system of the SCM.
2) Automatic alarm circuit design
The automatic alarm circuit is shown in Figure 3.5. The clock circuit consists of two 30P capacitors and a 12MHz crystal. The reset circuit is composed of a resistor, a capacitor, a diode, and a key switch, and has a function of power-on reset and manual reset. The INTO and INT1 of the microcontroller are connected to the theft and fire sensors, respectively, to achieve the collection of various alarm conditions. In order to prevent the influence of environmental interference signal on triggering the interrupt, when the interrupt is responded to, the interrupt signal is checked several times (for example, 5 times) and the interrupt signal is confirmed. Then the interrupt processing subroutine is executed, otherwise it is considered that the external interference signal is not Perform alarm processing to effectively reduce the chance of false alarms.
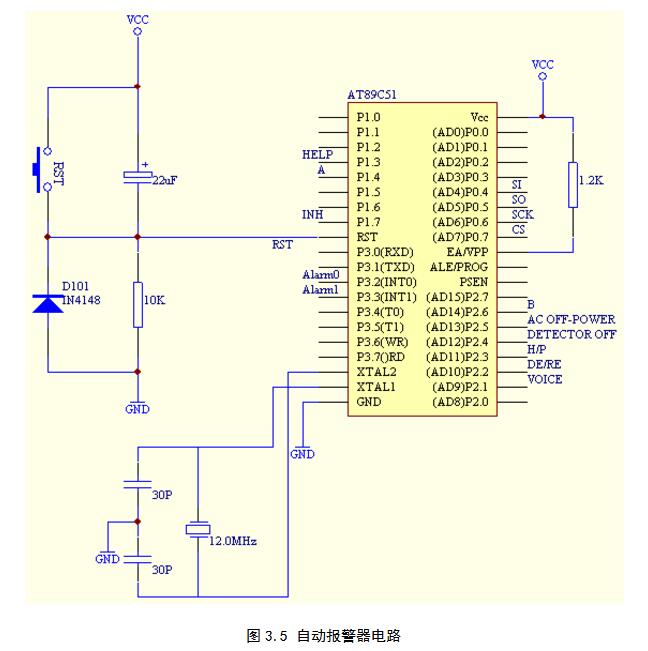
P2.1 is connected to the voice circuit to implement voice playback control. P2.2 connects the data transmission chip of the communication interface conversion chip and the receiving chip select terminal /RE (DE). P2.3 is connected with the telephone interface circuit to realize the control of the analog pick and drop machine. P2.4 then probe disconnection detection side, the microcontroller timing inquiry of the mouth, normal when the high level, when it detects a low level that is sent off the alarm 0. P2.5 connected to AC power failure alarm signal (DC power supply continued after the DC power supply, DC
After the power supply discharge is lower than the warning value, the DC alarm signal is sent to the automatic alarm device. P1.0, P1.1, and P1.2 are the three I/O ports that connect the keyboard circuit. P1.3 is connected to the emergency call button. P1.5 is connected to the serial clock input of the liquid crystal display, and P1.6 is connected to the data input of the liquid crystal display. P1.7 is connected to the chip select terminals INH and PI.4P2.6 of the multiplexer CD4051 respectively to the input terminals A and B of the multiplexer switch. The multiplex switch output is connected to the alarm LED and the buzzer respectively. When the alarm occurs, the output I/0 of the switch gives a high signal. PO.0, P0.1, P0.2, and PO.3 are connected to MT8888 DO, D1, D2, and D3, respectively, and serve as data buses. P2.0 is connected to the RSO of MT8888 and controls the selection of MT8888 internal registers. P2.7 is connected to the CS of the MT8888 and controls the MT8888 strobe.
P3.6 and P3.7 are connected to WR and RD of MT8888, respectively, to control the reading and writing of MT8888. P0.4 and P0.5 connect to EPROM serial input and serial output terminals, P0.6 and P0.7 connect to EPROM serial clock input and chip select input respectively.
4, automatic dialing and voice alarm circuit design
1) Dial circuit
The automatic dialing circuit designed by this system can realize automatic paging through the telephone network, send out a distress signal to the designated organization or personnel, describe the nature and location of the accident, and make rescue workers take corresponding measures to stop the accident. The main functions of the system are as follows:
1. Alarm priority function: The host computer shares a telephone line with the user's telephone set. When it is not alarmed, it does not affect the normal use of the telephone. Normal use of the telephone does not affect or interfere with the host alarm. When the host alarms, the priority is to make an alarm call.
2. Automatic dialing function: You can set up 1-6 groups of telephone or mobile number, each group does not exceed 15 digits.
3. The user can set and modify the password automatically for the automatic dialing alarm system.
4. It can record voice by itself: voice transmission, which is recorded by the user, and is recorded as “condition†(if anybody enters, fire, etc.), user’s name, address, and telephone number. Automatically detect the call status: When the alarm is detected, the usage status of the other party's telephone is automatically detected. If the other party is busy or no one is connected after ringing, keep the skip and wait for the next round of dialing.
5. Memory storage function: The system uses X25045 as the memory element, telephone number, alarm information and other input will not change because of power loss.
5, keyboard and password display circuit design
Keyboard and password display circuit is responsible for the system's contact with the outside world, data or command display, including: password input, change password input, phone number settings, emergency calls, recording, playback and other functions.
6, the design of the system power supply
1) Main power supply
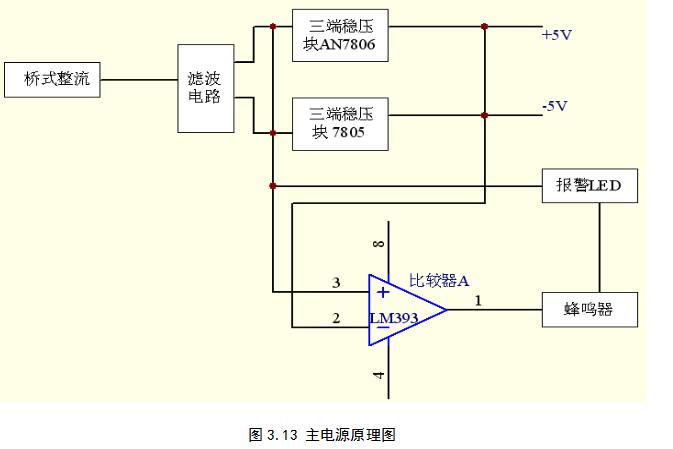
The main power supply of this system adopts 5V and 6V DC power supply. The schematic diagram is shown in Figure 3.13. The power supply circuit is a typical 7805/7806 application circuit with two power outputs. The circuit has a short-circuit protection function, the transformer output 7V AC, the bridge rectifier, capacitor filter, into the 7805 / 7806 input, and finally output sV / 6V DC. The resistor and red LED constitute the power supply indication circuit, and the green LED and buzzer are used for short-circuit alarm indication.
2) Backup power
Fire detectors should be monitored 24 hours a day without power outages. This requires the use of backup power. Using the backup power supply as the main power supply to supplement the power supply of the SCM system can prevent the SCM system from being suddenly powered off during operation, causing the data in the RAM of the computer system to be lost and interrupting the work. More importantly, it can avoid power interruptions. Causes the entire computer system to ask questions. The main function of the standby power supply is to supply battery power to the load when the input circuit is powered off. When the power supply is restored, the input circuit is responsible for supplying power to the load and charging the battery. Figure 3.14 is a schematic diagram of on-line standby power supply. It is a DC on-line backup power supply that can generate AC/DC power failure early warning signals in a timely, correct and reliable manner.
The ICL8212 is a high-performance programmable voltage detector that can operate normally with a low supply voltage (1.8V) and a wide range (1.8-30v). Its performance is minimally affected by the ambient temperature, and the entire supply voltage The range is also unaffected by changes in the supply voltage. When the detected voltage input to the 3-pin THRE (preset threshold input) is higher than 1.15V, the ICL8212 is a saturated transistor output, ie, the 3-pin OUT output is low; when the 3-pin is lower than 1.15V, 4 The pin outputs a high level, and this high level is still valid until the power supply drops to 0V. The HYST terminal of the 2 pin is a hysteresis voltage setting terminal. The hysteresis voltage setting prevents the detected voltage at the THRE terminal from being around 1.15V. , Make the OUT output in an unstable state.
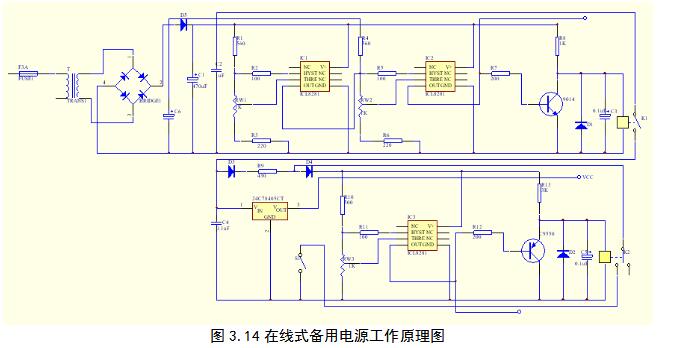
IC1, IC2 two pieces of ICL8212 constitute the window voltage detector, when the normal work, that is, the AC voltage in the normal operating range, the reasonable setting of the upper and lower detection threshold, the window voltage detector IC2 constituted by IC1, IC2 4 High-side output, transistor Q1 conduction, K1 relay pull-in, normal power supply work, unregulated DC all the way through the D3:, R9 to the rechargeable battery float charge, the other way to the system after the voltage regulator Stable DC voltage. Once AC loses power, the output of terminal 4 of the window voltage detector output IC2 is at a low level. It stores all the power-down information in the EEPROM of the automatic alarm device and the other way controls the transistor Ql. The AC circuit and voltage regulator are provided via the relay K1. The device is disconnected, and the rechargeable battery is continuously maintained to supply power to the system for a certain period of time (the length of time is determined by the capacity of the selected rechargeable battery), and a DC on-line uninterrupted power supply network is realized. After that, when the rechargeable battery is powered for a certain period of time and the voltage drops to a certain value (not to be discharged to a very low level), the DC undervoltage/power-down detector formed by IC3 stops the rechargeable battery through the transistor Q2 and the relay K2. System power supply. S1 is a manual switch. When the automatic alarm is running, it is closed and it is normally open.
As the demand for electric scooters continues to rise, we understand the importance of providing a reliable and safe power source for these vehicles. Our lithium battery packs are designed to meet these demands, featuring the latest lithium-ion technology and precise engineering to provide optimal performance and longevity. Our E Scooter Lithium Battery Packs are available in various voltage and capacity options, allowing you to choose the perfect fit for your electric scooter. Whether you need a lightweight, compact battery for easy portability or a higher-capacity battery for longer travel distances, we have you covered.
Light Electric Vehicle Battery,E Scooter Lithium Battery Pack,24V 210Ah Lifepo4 Battery Pack,24V Folklift Lifepo4 Battery
JIANGMEN RONDA LITHIUM BATTERY CO., LTD. , https://www.ronda-battery.com
